CyberSecurity
-
Would You Infect Someone Else With Ransomware To Save Your Own Files?
June 9, 2017Criminals are offering free decryption – if you help them infect other people’s computers. For more...
-
Five Tips to Stay Safe on Social Media While Traveling
June 9, 2017Oversharing your travel plans can put you, your colleagues, your corporate data systems, your property and...
-
Free Webinar on May 18th – Topic: Security Information and Event Management (SIEM)
May 8, 2017Security Information and Event Management (SIEM) – an organized approach to addressing security alerts generated by...
-
Do Not Open the Google Docs Email You Receive Today: It May Be a Scam
May 3, 2017There is a malicious Google Docs email that is spreading like wildfire right now — and...
-
How Posting On Facebook About 10 Concerts You Attended Can Get You Robbed
May 2, 2017Over the past few days a viral “survey” type post has been circulating around Facebook in...
-
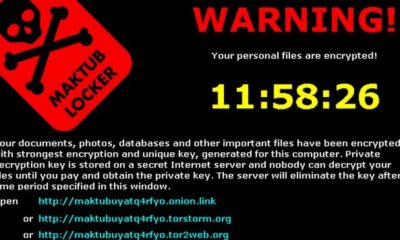
Over Half of Businesses Paying Ransomware Ransoms May Not Be Getting Their Data Back
May 2, 2017Ransomware is a form of cyber-attack in which criminals install malware (or trick victims into installing...
-
Google and Facebook Allegedly Duped in $100 Million Scam
May 1, 2017Google and Facebook were allegedly the victims (at least temporarily) of a $100-Million scam! To learn...
-
Amazon Wants to Put a Camera in Your Bedroom. What Could Go Wrong?
April 27, 2017Yesterday, Amazon revealed its new Echo Look, the first of its Alexa AI devices that can...
-
Russian Hacker Receives Record 27 Year Jail Sentence in USA
April 25, 2017Roman Valeryevich Seleznev, a Russian hacker also know by the hacker handles “Track2,” “NCUX,” and “Bulba,”...
-
7 Ways to Protect Your Twitter Account
April 12, 2017I recently authored a piece for IBM’s Security Intelligence blog about how to protect your Twitter...

















 CyberSecurity for Dummies is now available at special discounted pricing on Amazon.
Give the gift of cybersecurity to a loved one.
CyberSecurity for Dummies is now available at special discounted pricing on Amazon.
Give the gift of cybersecurity to a loved one.