Consolidating And Strengthening Internal Environment Protection: A High-Level Look At Cynet
One of the most powerful defense techniques against hackers who have invaded systems and networks is anomaly detection – that is, looking for behavior patterns that diverge from those that normally occur during business operations. Due to the combination of the failure of classic anti-virus solutions to stop many advanced attacks, the tremendous potential of anomaly detection to prevent hackers from actually doing anything after penetrating a network or system, and the growing industry-wide acceptance that even strongly-defended cyber-perimeters are likely to eventually be breached, products that offer anomaly detection have flooded the marketplace over the past decade.
Unfortunately, however, not only have severe breaches not stopped, but they seem to occur more often now than they did a decade ago – and many of today’s breaches involve the wholesale pilfering of sensitive data – an action that should always set off numerous red flags as anomalous. One of the reasons that anomaly detection engines have not succeeded in stopping such attacks, or in remotely reaching their potential, is that many such products are focused on individual sub-areas of anomalies – for example on anomalous network traffic – while ignoring others such as user behavior. Such offerings, for example, might miss an attack in which a particular user who rarely transmits files to the Internet begins transmitting the entire My Documents folder from a particular device to the Internet if another user regularly does so from that device.
Furthermore, today’s sophisticated cyber-criminals know about anomaly-detection technologies – and have already begun to craft attacks that seek to avoid detection by utilizing different types of techniques for penetrating, spreading, and performing nefarious payload functions (such as stealing data). Likewise, malware authors have been increasingly developing blended malware equipped with all sorts of stealth technology.
Even organizations that use a combination of multiple anomaly-detection technologies have suffered costly breaches; likely the result of a combination of factors: There is often an overlap between products (which causes time-wasting false alerts), a gap between products (which means that various anomalies remain undetectable), and no communication between the products (which means that anomalies that are only detectable after examining more than one aspect of a system cannot be detected). Furthermore, the deployment of anomaly-detection technology can be complex and technologically invasive, and the management of anomaly alerts extremely time consuming, thereby causing organizations to be unable to extract anywhere near the full potential security value of such systems.
Also, even with anomaly detection technology in place, there remains the challenge of actually managing and acting based on anomaly reports – visibility is not worth much if an organization lacks the resources to respond to potential attacks, and to protect itself going forward accordingly.
I was recently asked to take a look at Cynet – the brainchild of a team led by Eyal Gruner, the former child hacker who has founded several successful cybersecurity product firms. Cynet offers an internal-environments protection system that is armed with a consolidated version of multiple types of anomaly detection. The platform is available for a 14-day free trial or by requesting a personal demo.
There were several things that stood out to me about Cynet’s offering:
1. Consolidated visibility and point of control
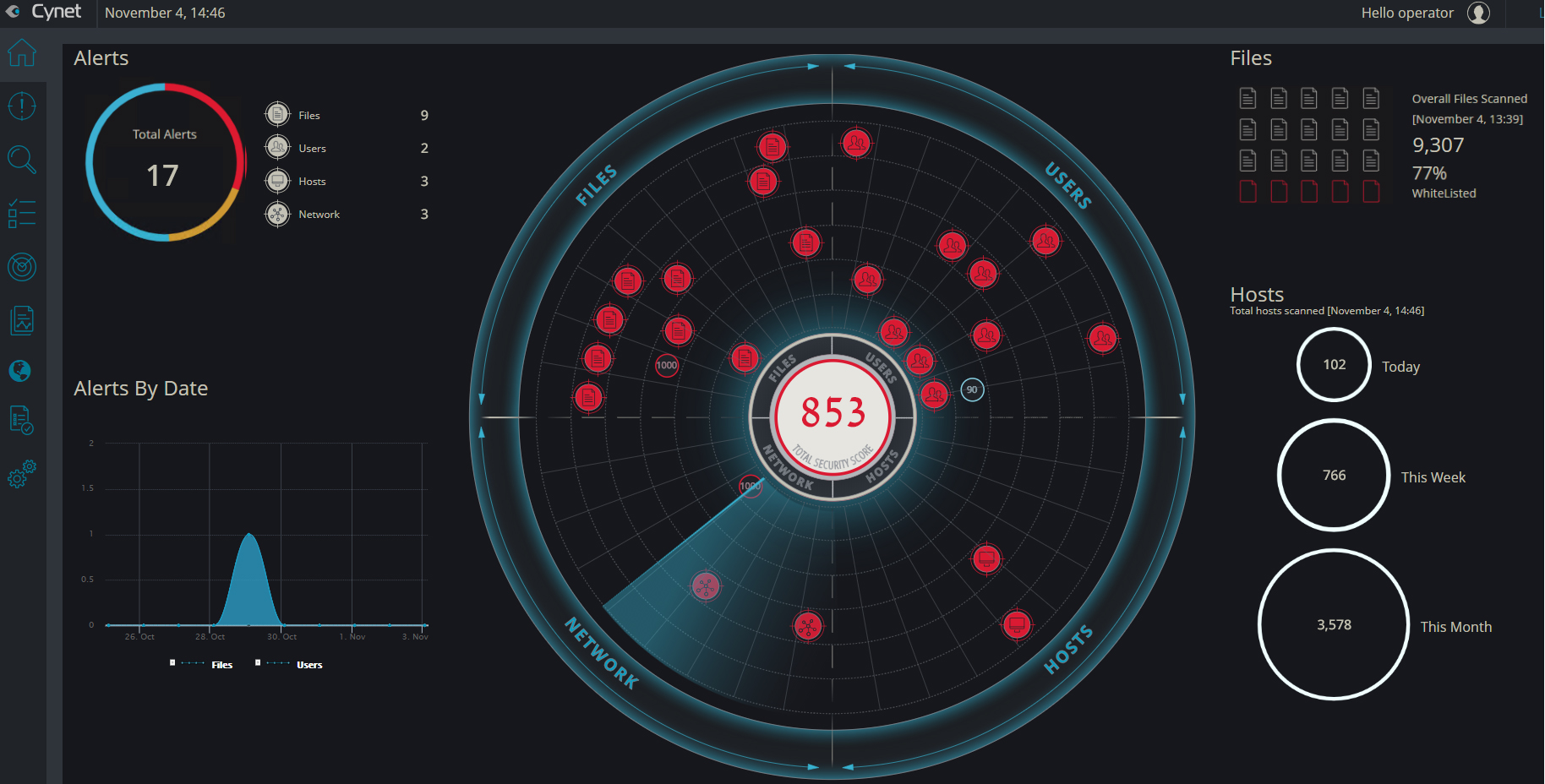
Maintaining visibility into the assets and activities transpiring within one’s infrastructure is obviously a critical element of any security program. Cynet provides combined visibility into the organization’s infrastructure, unifying the vantage p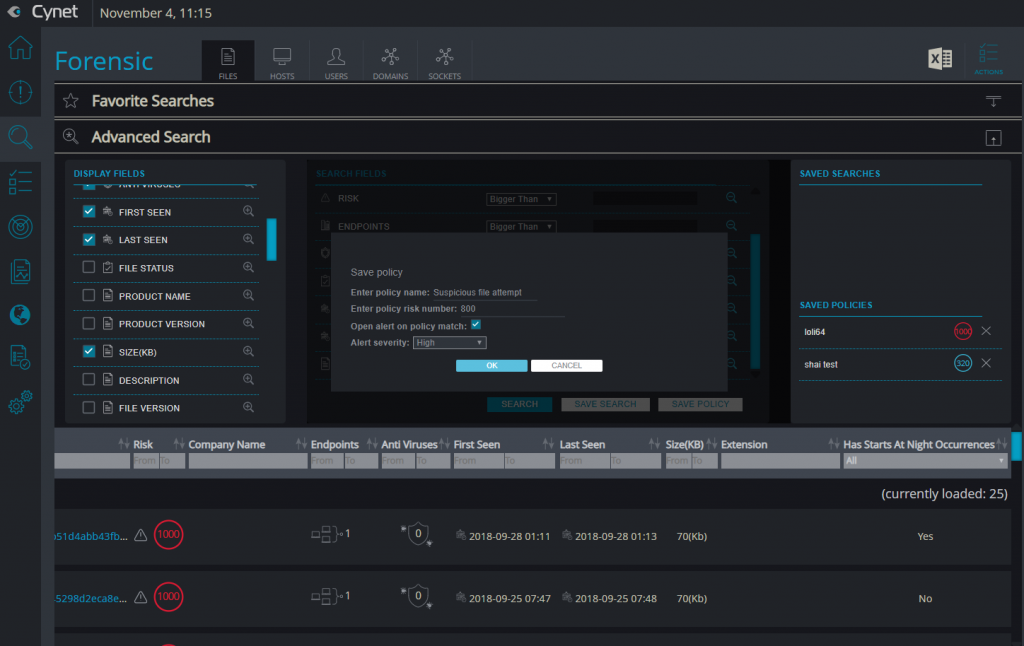
From the simplified dashboard, administrators can zoom in on any asset and examine its properties, configuration, and activity details, as well as see how it is interacting with other entities within the environment. Cynet also provides the ability to manage security from the same interface (as will be discussed later), as well as to perform various searches – with both built-in and customizable queries that can be saved and applied afterward as part of policies.
Of course, there are many security management tools on the market that can consolidate data from other security tools, but few can cross-correlate the data, and analyze it as such, in order to determine what to prioritize and display; manually integrating feeds from multiple products in order to achieve such data analysis is complicated, expensive, and prone to errors. Cynet’s approach seems to save time, improve efficiency, and reduce the likelihood of an administrator making a dangerous mistake.
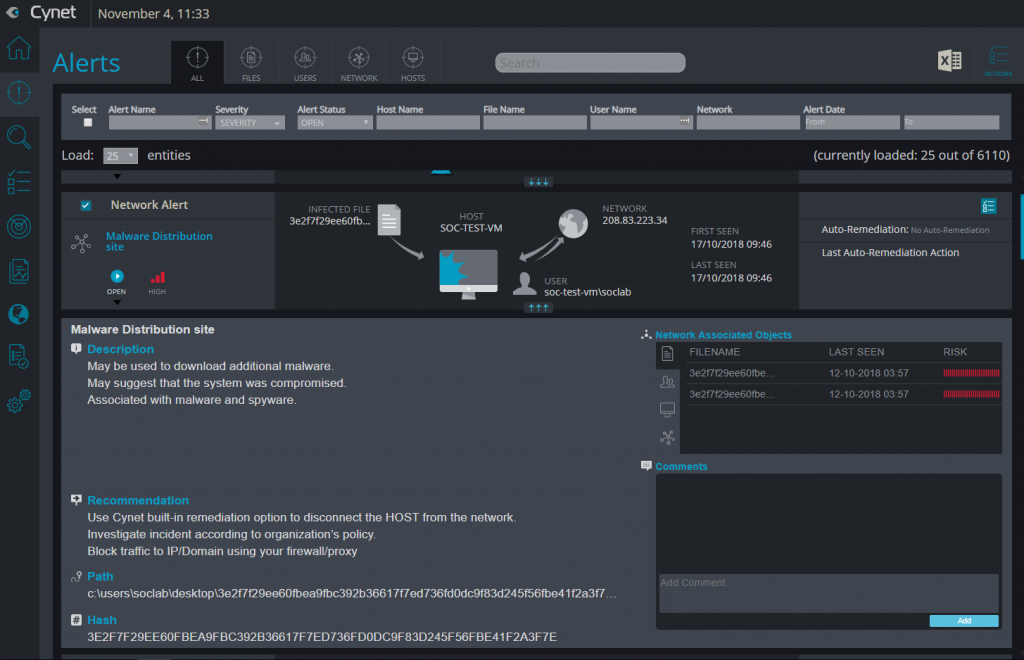
2. Detection and correlation of anomalies in all of the primary elements of an IT environment: Hosts, Networks, Users, and Files.
After installation and configuration, Cynet begins by mapping and learning the entire environment that it seeks to protect: continuously collecting data on host configurations, files (executable and otherwise), process execution, network traffic, and user activities. Most endpoint solutions focus on one or two of these areas – so getting all four in a single product would appear to offer major benefits: consolidating all four areas isn’t a matter of just addressing more types of anomalies – some anomalies can only be detected if one combines knowledge of expected behaviors in multiple areas.
For example, most modern data-exfiltration attacks do not involve any process anomalies – it is only by monitoring network traffic (and, sometimes, only by doing so on a per user basis) that such attacks can be detected, yet, when it comes to ransomware attacks – which typically operate through malicious file execution on an endpoint, monitoring network traffic or user activities may produce no sign of any anomalous activities.
Also, consider the case of users logging into an organizational information resource for the first time. Of course, such logins are always risky, as they may or may not be malicious, yet, they obviously cannot be blocked in general as matter of policy; it is only by correlating the login activity with the executed processes and hosts associated with the relevant users that an anomaly-detection system can connect the dots to accurately determine whether situations are benign or likely malicious.
Of course, getting all four areas of analysis – hosts, networks, users, and files – in a single security system also simplifies the management of information security, and can potentially reduce both errors and dollar costs when compared with buying multiple products and trying to integrate them to work together. As criminals continue to increasingly utilize blended attacks and malware, the value of a simplified approach to detecting attacks exploiting multiple vectors is likely to grow.
3. Ability to respond in all of the primary elements of an IT environment: Hosts, Networks, Users, and Files.
Because successful cyberattacks often entail the abuse of multiple entity types – hosts, on which attackers execute code remotely, user accounts whose credentials are stolen and abused so as to gain access to sensitive resources, network traffic for both the attacker’s command and control activities and for transmitting sensitive data out of the victim’s network, and running malic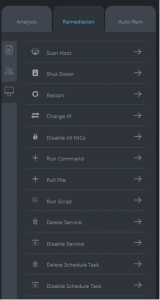
As it did vis-à-vis visbility, the Cynet interface presents administrators with a single console from which they can take action in all of these areas. Responders can, for example, disable user accounts or reset users’ passwords, block network traffic to malicious destinations, delete or quarantine suspicious files, and kill malicious processes. Administrators can even act with surgical precision on hosts – for example, by removing a single schedule task or deleting an individual service – which allows for remediating problems without disrupting operations by taking entire systems offline.
Cynet also lets administrators build response playbooks using customized remediation policies, and offers them the ability to orchestrate a cross-environment response through the use scripts that can be transmitted to other components within the infrastructure (for example, firewalls or an Active Directory). And, yes, there are many detailed screens that provide all sorts of technical details to satisfy those who wish to see them – but, one of the system’s strengths seems to be that one does not need to be a technical expert to use much of the core product.
4. Advisory service
Cynet offers at no additional cost to its customers what is calls “CyOps” – a de facto 24×7 security operations team – that serves as both a proactive advisor service (e.g., someone from CyOps will contact a customer if there is some new risk that that party needs to know about), and a reactive forensics team (e.g., doing the post-mortem analysis in the event of an incident). CyOps allows Cynet customers to benefit from security knowledge gained as the result of attacks launched against other Cynet customers, as well as from intelligence garnered by Cynet’s analysis of malware samples collected from throughout its customer ecosystem.
The bottom line is that Cynet’s approach makes sense, improves upon today’s market-standard offerings, and can potentially simultaneously improve security, simplify management, and reduce associated costs – especially for organizations that lack the large cyber-armies and technology arsenals of major financial institutions and other Fortune 500 companies.
This post is sponsored by Cynet.











 CyberSecurity for Dummies is now available at special discounted pricing on Amazon.
Give the gift of cybersecurity to a loved one.
CyberSecurity for Dummies is now available at special discounted pricing on Amazon.
Give the gift of cybersecurity to a loved one.