Giving Smaller Businesses The Critical Power Of Large Community Threat Intelligence: A High-Level Look at CrowdSec
As I discussed last month, smaller businesses continue to suffer a disproportionate share of severe cyber-breaches, and a significant percentage of those organizations that are successfully penetrated go out-of-business within a year as a result.
One significant contributing factor to the danger faced by smaller firms is that once they are large enough to operate their own infrastructure, their security teams and technologies often function primarily in a reactive mode, a problem caused, at least in part, by a lack of access to easily-actionable cyber-threat intelligence that would allow defenders to leverage more strategic, proactive approaches. Of course, in the context of cybersecurity, threat intelligence refers to information about hostile actors and/or the threats that they pose – security teams that have the ability to utilize such information can often dramatically improve their security posture by both proactively blocking parties that third-party security teams and technologies have already determined are hostile, as well as by improving the selecting of what tasks to do when – basing to-lists and priorities on what dangers pose the greatest real world danger, rather than just theoretically posing the greatest risks.
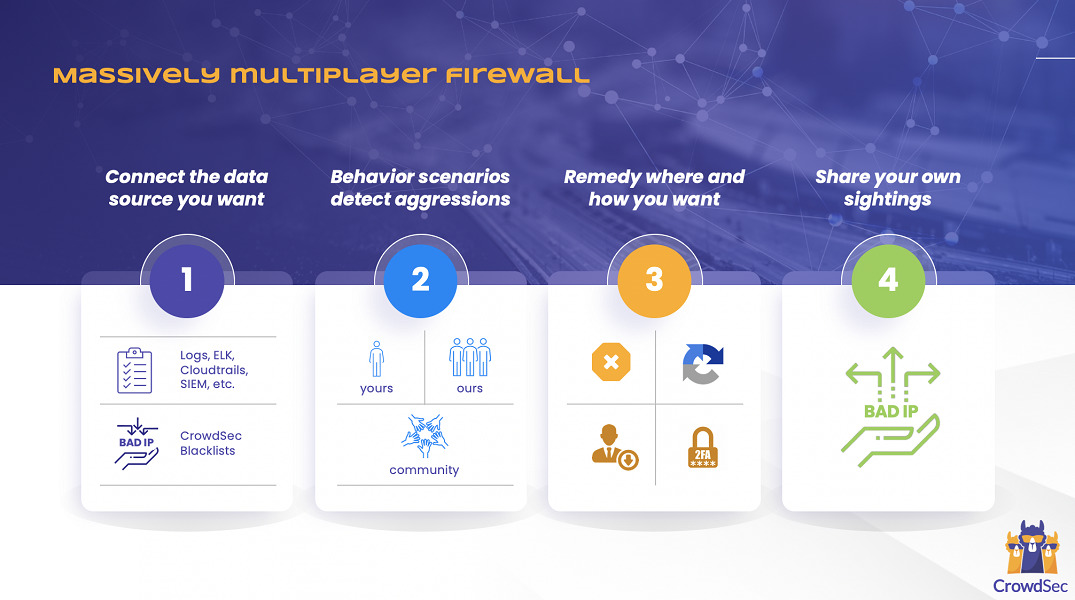
I was recently asked to take a look at CrowdSec – a new, free, open-source information security technology created in France that seeks to improve the current situation. In some ways, CrowdSec mimics the behavior of a constantly-self-updating, massive, multi-party, and multi-network firewall. Like a classic network-layer firewall, CrowdSec allows administrators to configure all sorts of OSI Middle Level (i.e., Levels 3 Network and Level 4 Transport) rules. And, similar to other intrusion prevention technologies like Fail2ban, CrowdSec offers the ability to block traffic in real time if the traffic appears to come from IP addresses and ranges deemed potentially dangerous based on an analysis of prior traffic received from such sources.
Like many other offerings, CrowdSec operates in real time, but can also analyze logs of earlier traffic to look for potential danger – and can leverage such analysis when making future real-time decisions.
CrowdSec, however, does not base its analysis of traffic solely on earlier traffic received by the local site – it leverages the entire community of CrowdSec users to study traffic and determine what seems to pose the greatest risks.
One might think of CrowdSec as almost a group or crowdsourced version of Fail2ban – in which information about device trust and reputation levels – for example, that a machine at a particular IP address is engaging in irregular and/or dangerous behavior – is shared across the entire authorized community in real time once the information has been vetted by the CrowdSec algorithms. As a result, if hackers begin to attack just a few members of the CrowdSec community, ALL members may know to proactively block access from the devices from which the malicious traffic is emanating – and they may know this BEFORE the first packet from such devices even arrives at their own external firewalls. Furthermore, the process of taking action based on such information can be automated – so an attack against members of the community on one side of the planet can lead to preventive measures being taken seconds later by others on the opposite side of the globe.
As such, CrowdSec effectively automates the generation of firewall rules based on both the analysis of local inbound traffic as well as a community-powered IP reputation system, making it a defense mechanism that supplements classic firewalls, and that becomes increasingly powerful as its community of users grows. CrowdSec released version 1.0 at the end of 2020, and reported to me that its technology is already being used in over 70 countries across all six continents (other than Antarctica).
I should also note that CrowdSec’ s rules are not limited to constraining TCP/IP and UDP/IP; it allows different types of risks, and levels of risk, to be addressed in different ways at the application level – for example, traffic from some offending IPs may be entirely blocked, while other “risky devices” may be allowed to communicate as long as users coming from such addresses utilize multifactor authentication for access instead of just a password, while other questionable devices may be granted access only after a user successfully completes a captcha or other anti-bot test.
I have intentionally kept this piece at a high level – as the reality is that as security technologies go, the CrowdSec system is pretty simple to set up and operate. The offering does provide an API and is both decentralized and interoperable, and the team even recently released a WordPress plugin that automates much of the setup for those who want to use the security technology specifically to defend a WordPress website (or websites), and there are built in hooks for integrating with Metabase for reporting and analysis. (For those who prefer, CrowdSec can also generate Prometheus data to feed into Grafana or the like.)
Of course, there are multiple competing commercial offerings that have been available for quite some time – and larger organizations are certainly using such technologies en masse. There are also threat intelligence feeds that are effectively free, but, in general, their contents have tended not to be easily actionable, sometimes requiring considerable resources in order to be put it into practical use. Some such systems have been able to provide earlier recognition of potential problems than might have otherwise been achievable without paying, but, at the same time, have not been close enough to real time to truly address many serious risks. Others have been unable to generate sufficiently granular data so as to easily deliver improved security without introducing unacceptable levels of false or exaggerated positives. Others have offered poor reporting and integration with reporting tools. That said, existing offerings will improve, and new ones will be introduced. Either way, while it is still too early to know where the dust will ultimately settle when it comes to open-source threat intelligence, it is safe to say that there is going to be greater use of open-source threat intelligence offerings in the future than there is today.
On that note, therefore, for the many smaller businesses that have resisted investing in pre-existing commercial and open-source threat intelligence offerings due to perceived associated costs, either in terms of dollars, time, or increased complexity, CrowdSec looks like an interesting option to explore. While open source offers both advantages and disadvantages, one of the big plusses for those of us responsible for taking a look at new technologies is that we can download and test open-source technologies without having to pay, and without spending time negotiating agreements or obtaining budget approvals. Additionally, one can easily run CrowdSec on logs before choosing to go “live” – and, as such, you can quickly get a pretty good picture whether CrowdSec might help you do your job better and with reduced manual intervention. So, if you are responsible for information security and are not both getting and utilizing actionable IP threat intelligence, it may be wise to download and take a look at CrowdSec.
This article is sponsored by CrowdSec, which recently released a free, open-source security engine for websites that allows businesses to identify and seamlessly share with one another information about risky devices attempting to connect – thereby improving security for the entire community of users.











 CyberSecurity for Dummies is now available at special discounted pricing on Amazon.
Give the gift of cybersecurity to a loved one.
CyberSecurity for Dummies is now available at special discounted pricing on Amazon.
Give the gift of cybersecurity to a loved one.